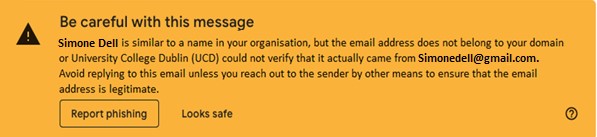
If you suspect you have received a phishing email, there are a number of steps to take that we would like you take before contacting us. It is a great benefit for us to have this information as soon as possible.
First steps
- Do not click any links
- Do not open any attachments
- Do not enter any personal details on the fraudulent email or website
- Open the email in UCD Gmail
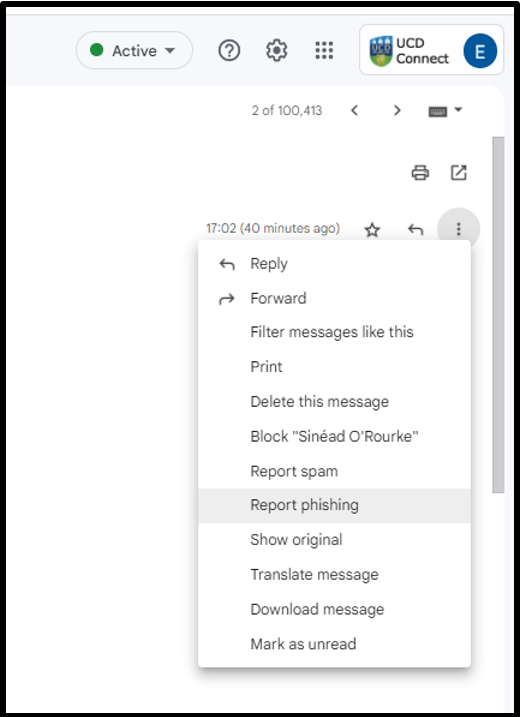
- Report/mark the email as phishing in Gmail
- Inform your colleagues
Need more help?
- Contact us and include the following details in your call
- A screenshot or copy of the email. (The email may now be in your Spam folder)
- The reason why the email is suspicious
- The (opens in a new window)header information for the suspicious email