Phishing
Phishing is a technique used by criminals to steal personal or financial information such as your passwords, date of birth, credit card details, etc. Identity thieves try to lure you into giving up personal or financial information by making what looks like a legitimate request from an organisation you trust. These might look like they are from a bank, credit card company, or even UCD. Unfortunately, phishing scams can be highly effective and numerous students and staff have been tricked.
Please remember IT services will never ask you for your password.

How to spot a phishing email
You can protect yourself from phishing attacks by taking the initial step of learning how to spot a phishing email. There are a number of typical warning signs to look out for.
- Use the Gmail web client and Gmail mobile app instead of email clients such as Outlook, native iPhone clients, etc. Gmail includes University specific warning messages when it detects that a staff email account is being impersonated or spoofed, such as Gmail Phishing Warning
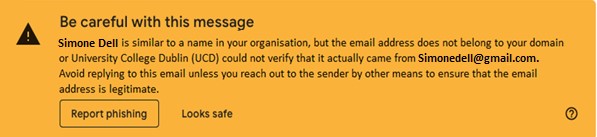
- Look for the signs. Does the email contain a generic greeting, is it urgent or threatening, has poor spelling or grammatical errors, making an offer that seems too good to be true? Then you should be suspicious!
- Do not click on any web links or scan QR Codes. Avoid clicking on any links or scanning QR codes in the email, especially if the email is from an unknown or suspicious.
- Always verify web links and never open unexpected attachments. Get into the habit of typing URLs into your browser. Don’t open attachments unless you’re expecting a file from someone. Give them a call to verify if you’re suspicious.
- Call to verify. Let’s say you receive an email claiming to be from someone you know, a friend, colleague, or even the President of the university. Cybercriminals often spoof real addresses to convince you, then request that you perform an action such as transfer funds or provide sensitive information. If something seems off about the email, call them on a trusted number to confirm the request. Do not trust the contact details in the email as they may also be fake.
- Check the reply email address. Phishing emails often impersonate staff details such as names, include photos, company logos, phone numbers, etc. A sender’s email address can be easily faked and can be completely different to the reply email address, so always check the reply address before sending.
- Never share your password. Your password is the key to your identity, your data, and your classmates’ and colleagues’ data. It is for your eyes only. IT Services IT helpdesk will never ask you for your password.
- Phishing isn’t relegated to just email! Cybercriminals will also launch phishing attacks through phone calls, text messages, or other online messaging applications. Don’t know the sender or caller? Seems too good to be true? Then it is probably a phishing attack.
- Trust your instincts. If you think it is suspicious then it probably is!
Phishing examples: What to look for?
What should I do if I receive a Phishing email?
If you suspect you have received a phishing email, there are a number of steps to take that we would like you take before contacting us. It is a great benefit for us to have this information as soon as possible.
First steps
- Do not click any links
- Do not open any attachments
- Do not enter any personal details on the fraudulent email or website
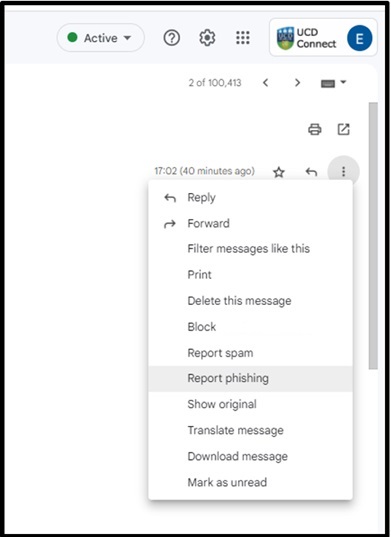
- Open the email in UCD Gmail
- Report/mark the email as phishing in Gmail
- Inform your colleagues
Need more help?
- Contact the IT Helpdesk by calling 01-7162700 or go to the (opens in a new window)IT Support Hub. Include the following details in your call:
- A screenshot or copy of the email. (The email may now be in your Spam folder)
- The reason why the email is suspicious
- The (opens in a new window)header information for the suspicious email

What do I do if I responded to a phishing email?
If you believe you have been phished by either clicking on a untrusted link, entered your login details on a fake website, opened an untrusted attachment, etc.take the following actions:
- Change your password immediately. Change your UCD Connect password using UCD's(opens in a new window) Password self service on a trusted computer (If you opened an attachment that may contain malware, use another computer/device).
- If you used your University account details (email and password) when creating personal online accounts, you should also check recent activity on these accounts and change the account password e.g. Online Bank account, Pay pal etc. Please ensure the your UCD passwords are UNIQUE and not used for any personal accounts.
- Run an antivirus scan. Scan your machines using UCD's Sophos Intercept X for virus and malware. Take note of any malware discovered before you quarantine or delete the suspicious files and provide these details to the IT Helpdesk.
- Report it. The IT Helpdesk and IT Security team are here to help, so if you suspect that your account is at risk then please report the incident to the IT Helpdesk by calling 01-7162700 or go to theIT Support Hub. Include the following details:
- A screenshot or copy of the email. (The email may now be in your Spam folder)
- The (opens in a new window)header information for the suspicious email
- The reason why you believe the email is suspicious
- A screenshot of the Sophos scan results (if available)
- Check recent account activity. Run a (opens in a new window)Google Security check-up to check (opens in a new window)recent account activity and (opens in a new window)find out who else has access to your University information.
- Check the security and settings of your accounts. Hackers often change the setting of accounts, such as adding automatic email forwarding, filters, adding new accounts or changing email signatures. Details on how to check the security, settings and recent account activity of your University email account is outlined (opens in a new window)here.
- Is your computer still acting strange?It might be best to start from scratch with a complete rebuild (factory reset) of your work device or work computer so you can be sure that all suspicious software has been removed. The Helpdesk will arrange for an IT Support person to contact you to help clean or rebuild the UCD Staff owned computer. Please ensure to backup any important documents, photos, etc. before rebuilding a device.
- Update your mobile software and apps. Make sure your mobile device is secure by reviewing(opens in a new window) IT Security's recommendations
- Self-report to credit agencies. If you believe your personal information is at risk, such as bank account numbers, PPS number, etc. you should contact your Bank, Revenue, etc. to inform them of the incident.
- Be prepared with backups. Backup your files frequently.
- Stay ahead of the hackers. Check the Have-I-been-pwned (opens in a new window)website to see if your University or personal email addresses were discovered in external data breaches.
Take UCD's Phishing Challenge
Take UCD's interactive Phishing Challenge today to see real examples of phishing emails, spot fake URL's and find out how to avoid being scammed. It only takes 5 minutes and can save you hours of stress.
UCD IT Services
Computer Centre, University College Dublin, Belfield, Dublin 4, Ireland.Contact us via the UCD IT Support Hub: www.ucd.ie/ithelp